1. sysmon Download : https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
Sysmon - Windows Sysinternals
Monitors and reports key system activity via the Windows event log.
docs.microsoft.com
2. sysmon config file : https://github.com/SwiftOnSecurity/sysmon-config
GitHub - SwiftOnSecurity/sysmon-config: Sysmon configuration file template with default high-quality event tracing
Sysmon configuration file template with default high-quality event tracing - GitHub - SwiftOnSecurity/sysmon-config: Sysmon configuration file template with default high-quality event tracing
github.com
3. 설치 진행 : 최초 설치 -l, 변경 적용 -c
Sysmon64.exe -accepteula -i C:\Users\Administrator\Desktop\Sysmon\sysmonconfig-export.xml -l -n
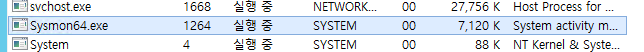
4. 설치 확인
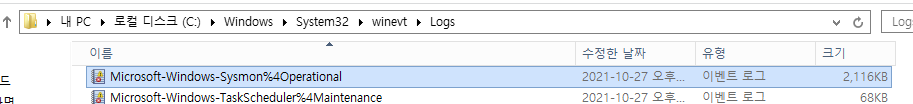
5. 로그위치 : C:\Windows\System32\winevt\Logs
6. 이벤트 뷰어 확인

7. 참조 Event Code
| Event ID | 설명 |
| 1 | 프로세스 생성 |
| 2 | 프로세스가 파일 생성시간을 변경 |
| 3 | 네트워크 연결 |
| 4 | Sysmon 서비스 상태 변경 |
| 5 | 프로세스 종료 |
| 6 | 드라이버 로드 |
| 7 | 이미지 로드 (“-l” 옵션으로 활성화 필요) |
| 8 | 다른 프로세스에서 스레드 생성 |
| 9 | RawAccessRead 탐지 (프로세스가 “\\.\” 표기법 이용하여 드라이브 접근시) |
| 10 | 특정 프로세스가 다른 프로세스 Access (ex. Mimikatz > lsass.exe) |
| 11 | 파일 생성 (생성 및 덮어쓰기) |
| 12 | 레지스트리 이벤트 (키 값 생성 및 삭제) |
| 13 | 레지스트리 이벤트 (DWORD 및 QWORD 유형의 레지스트리 값 수정) |
| 14 | 레지스트리 이벤트 (키 및 값 이름 변경) |
| 15 | FileCreateStreamHash (파일 다운로드와 관련된 Zone.identifier 확인) |
| 17 | PipeEvent (파이프 생성) |
| 18 | PipeEvent (파이프 연결) |
| 19 | WmiEventFilter 활동이 감지 됨 (악성코드 실행시 사용될 가능성 있음) |
| 20 | WmiEventConsumer 활동이 감지 됨 |
| 21 | WmiEventConsumerToFilter 활동이 감지 됨 |
| 255 | Sysmon 오류 |
8. winlogbeat download : https://www.elastic.co/kr/downloads/beats/winlogbeat
Download Winlogbeat | Ship Windows Event Logs | Elastic
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
www.elastic.co
9. winlogbeat.yml
winlogbeat.event_logs:
...
- name: Microsoft-Windows-Sysmon/Operational
...
# ------------------------------ Logstash Output -------------------------------
output.logstash:
# The Logstash hosts
hosts: ["10.10.10.230:5044"]
10. 설치
PS C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64> .\install-service-winlogbeat.ps1
11. 테스트
PS C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64> .\winlogbeat.exe test config -c .\winlogbeat.y
ml -e
2018/03/16 06:55:58.025085 beat.go:436: INFO Home path: [C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64] Config path: [C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64] Data path: [C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64\data] Logs path: [C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64\logs]
2018/03/16 06:55:58.025085 metrics.go:23: INFO Metrics logging every 30s
2018/03/16 06:55:58.026092 beat.go:443: INFO Beat UUID: 5ef661c8-806f-465d-b3db-5f1d4def5309
2018/03/16 06:55:58.029186 beat.go:203: INFO Setup Beat: winlogbeat; Version: 6.1.1
2018/03/16 06:55:58.030192 client.go:123: INFO Elasticsearch url: http://localhost:9200
2018/03/16 06:55:58.030192 module.go:76: INFO Beat name: DESKTOP-AKG019N
2018/03/16 06:55:58.030192 winlogbeat.go:56: INFO State will be read from and persisted to C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64\data\.winlogbeat.yml
Config OK
12. 서비스 실행 및 중지
PS C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64> Start-Service winlogbeat
PS C:\winlogbeat-6.1.1-windows-x86_64\winlogbeat-6.1.1-windows-x86_64> Stop-Service winlogbeat
13. logstash conf
input {
beats {
port => 5044
}
}
filter {
if ([event_data][hashes][altsha1]) {
mutate {
split => ["[event_data][hashes][altsha1]" , "="]
add_field => { "[event_data][hashes][sha1]" => "%{[event_data][hashes][altsha1]][1]}" }
remove_field => [ "[event_data][hashes][altsha1]"]
}
}
if ([event_data][hashes][altmd5]) {
mutate {
split => ["[event_data][hashes][altmd5]" , "="]
add_field => { "[event_data][hashes][md5]" => "%{[event_data][hashes][altmd5]][1]}" }
remove_field => [ "[event_data][hashes][altmd5]"]
}
}
if ([event_data][hashes][altsha256]) {
mutate {
split => ["[event_data][hashes][altsha256]" , "="]
add_field => { "[event_data][hashes][sha256]" => "%{[event_data][hashes][altsha256]][1]}" }
remove_field => [ "[event_data][hashes][altsha256]"]
}
}
if ([event_data][hashes][altimphash]) {
mutate {
split => ["[event_data][hashes][altimphash]" , "="]
add_field => { "[event_data][hashes][imphash]" => "%{[event_data][hashes][altimphash]][1]}" }
remove_field => [ "[event_data][hashes][altimphash]"]
}
}
if ([event_id] == 1) {
grok {
match => { "message" => "http://%{IP:[remote_ip]}/%{GREEDYDATA:[event_data][powershell_file]}'" }
}
}
}
output {
stdout { codec => rubydebug }
elasticsearch {
hosts => ["localhost:9200"]
index => "logstash-winlogs"
}
}'Monitoring Tools > ELK Stack' 카테고리의 다른 글
| 10. xpack security 적용 (0) | 2022.04.26 |
|---|---|
| 9. Elasticsearch 상태 정보 보기(cluster, shard, index, node) (0) | 2022.04.26 |
| 7. Elastalert (0) | 2022.04.26 |
| 6.2 filebeat offset 초기화 (0) | 2022.04.22 |
| 6.1 filebeat multiple indexing (0) | 2022.04.22 |
